Beyond the Security Bottleneck: Why AppSec-as-a-Service is Your Development Team's Secret Weapon
May 20, 2025 By Steve Kosten, and Aaron Cure In Technical
In today's high-velocity development environment, security teams are facing an impossible equation: protect an ever-expanding application landscape with increasingly limited resources while not slowing down innovation. This tension has created what many organizations experience as the "security bottleneck" – where application security becomes the constraint that prevents rapid, continuous delivery of new or updated applications. But what if application security could transform from your biggest
bottleneck into your development team's secret weapon? The cybersecurity talent gap has reached crisis levels, with over 3.4
million unfilled positions globally. This shortage hits application
security particularly hard, as this specialized discipline requires deep
understanding of both security principles and modern development
practices. The consequences of this resource constraint are severe: Security debt: With insufficient resources to address
vulnerabilities promptly, organizations accumulate "security debt"
that becomes increasingly expensive to resolve. Delayed releases: Without adequate application security staff,
critical reviews and assessments create bottlenecks. Vulnerability backlogs: Security teams prioritize only the most
critical issues, leaving other vulnerabilities unaddressed. Large
amount of false positives resulting from scanners overwhelm the
teams even more in clearing the backlogs. Developer frustration: When security guidance is delayed or
vague, developers waste time or implement incomplete fixes. The financial implications of application security are straightforward
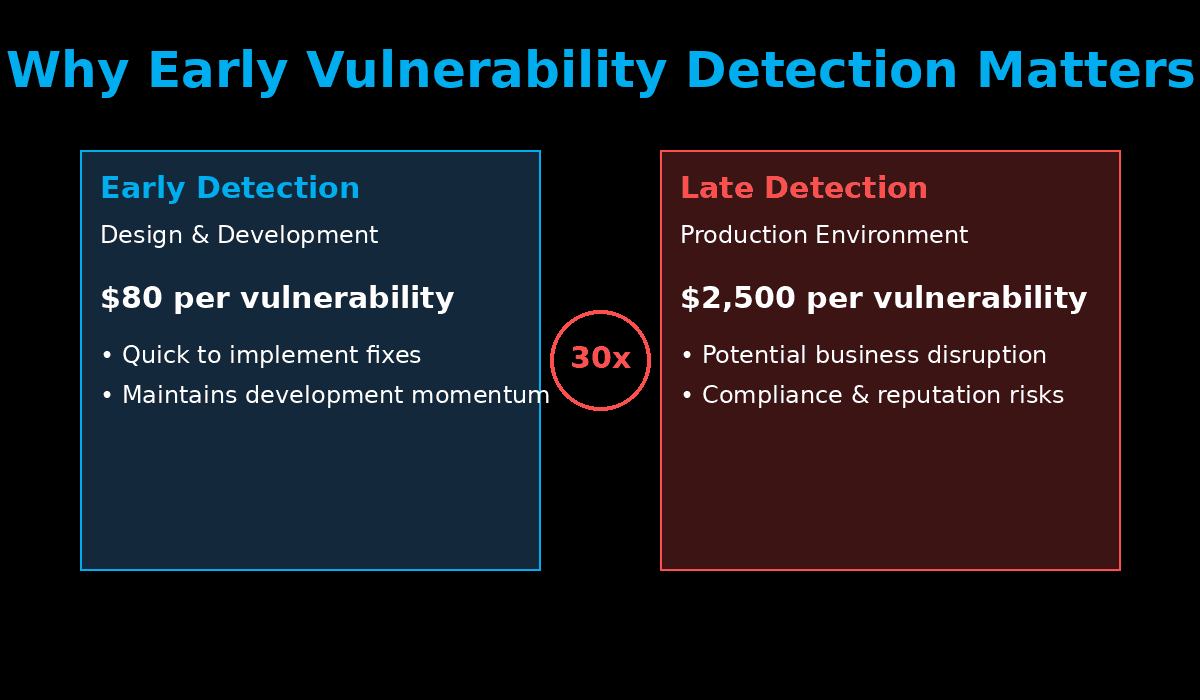
but often overlooked: vulnerabilities found early in the SDLC cost
dramatically less to fix than those discovered in production. According
to industry research, fixing a vulnerability discovered during design or
coding phases costs about $80, while the same vulnerability found in
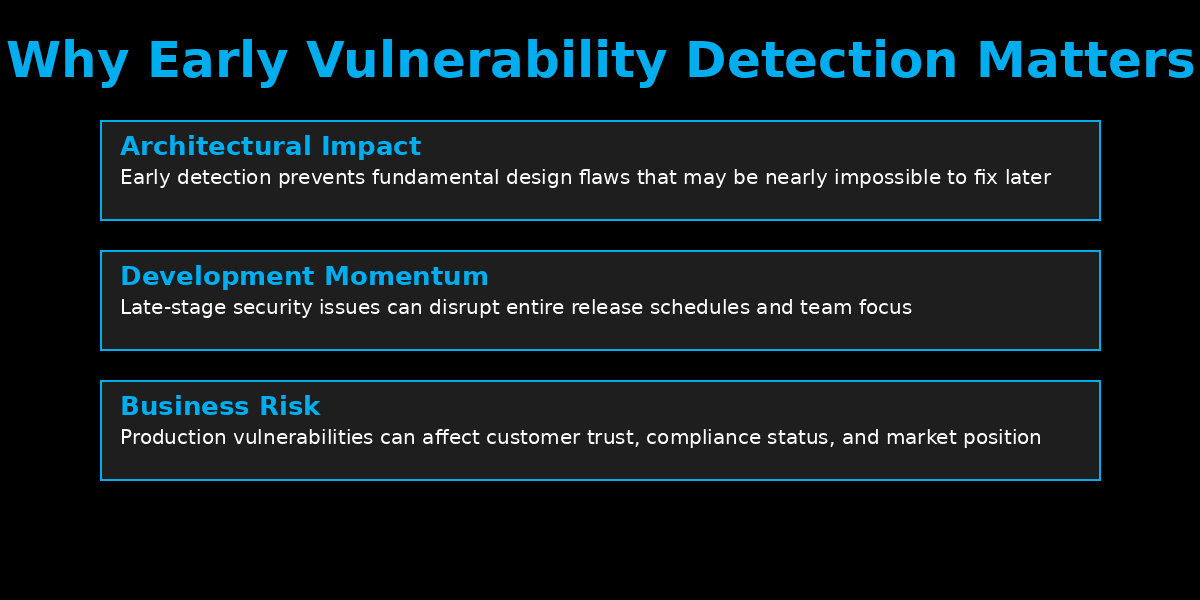
production costs approximately $2,500 – a 30x increase. This cost multiplier goes beyond just the financial impact: Architectural implications: Early-stage vulnerability detection
can prevent fundamental design flaws that may be nearly impossible
to fix later. Development momentum: Late-stage security issues can disrupt
entire release schedules and dev team focus. Business impact: Production vulnerabilities can affect customer
trust, compliance status, and market position. The challenge, of course, is having the right application security
expertise available at the right development stages to identify these
issues early. While many organizations have invested in automated security tools to
compensate for limited security personnel, these tools create a new
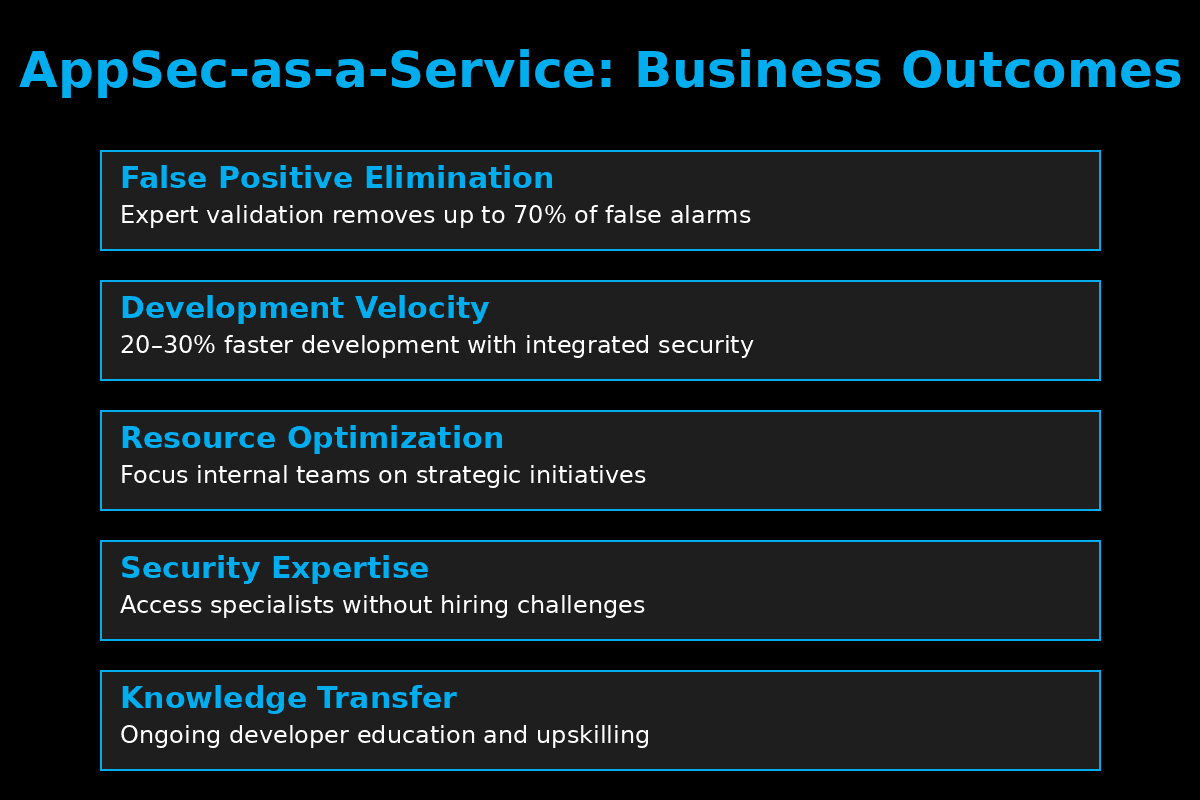
problem: false positives. A recent study found that up to 70% of
security alerts generated by automated tools turn out to be false
positives or low-risk issues that don't warrant remediation. This creates several cascading problems: Alert fatigue: Developers and security professionals become
desensitized to warnings. Wasted engineering time: Valuable development resources are
spent investigating non-issues. Missed critical vulnerabilities: Real threats get lost in the
noise. Deteriorating security culture: When tools cry wolf repeatedly,
security loses credibility. What's needed isn't just more scanning – it's expert human judgment to
contextualize, validate, and prioritize findings in ways that automated
tools simply cannot. This is where Application Security as a Managed Service (or
AppSec-as-a-Service) enters as a strategic solution. Rather than
struggling to build a complete in-house application security team – an
increasingly difficult proposition given the talent shortage –
organizations can extend their capabilities through specialized
partners. The most effective AppSec-as-a-Service solutions act as force
multipliers by providing: 1. Contextual Vulnerability Validation Expert security professionals validate and contextualize automated
findings, eliminating false positives and providing meaningful risk
assessments based on your specific business context. 2. Practical Remediation Guidance Rather than vague vulnerability reports, developers receive specific
guidance – sometimes even including code examples – on how to fix issues
effectively. 3. SDLC Integration Expertise Security experts help integrate security checkpoints throughout your
development lifecycle with your systems, ensuring vulnerabilities are
caught at the optimal time without creating bottlenecks. 4. Security Debt Management Managed services can help prioritize existing vulnerability backlogs,
creating realistic remediation roadmaps that align with business
priorities. 5. Knowledge Transfer Beyond just finding and fixing vulnerabilities, effective AppSec
partners help upskill development teams, gradually reducing dependency
on external resources. The ROI calculation for AppSec-as-a-Service becomes compelling when
considering: Cost avoidance: Preventing just one significant breach (average
cost: $4.88 million) easily justifies the investment. Accelerated development: Removing security bottlenecks and false
positives can improve development velocity by 20-30%. Resource optimization: Internal security resources can focus on
strategic initiatives rather than routine vulnerability management. Compliance efficiency: Expert partners can streamline security
compliance activities. Scalable security: AppSec resources can flex with development
needs without the overhead of hiring. In today's threat landscape, where every organization faces both talent shortages and escalating cyber risks, AppSec-as-a-Service isn't merely a cost-effective solution—it's a strategic investment that transforms security from your greatest vulnerability into your strongest competitive advantage. One of the most valuable aspects of a managed application security
approach is transitioning from "fix everything" to focused remediation.
When working with limited resources, prioritization becomes critical. Effective remediation strategies include: Business impact analysis: Prioritizing vulnerabilities affecting
critical business functions or sensitive data. Exploitation difficulty assessment: Evaluating how easily
vulnerabilities could be exploited in your specific environment. Root cause analysis: Identifying underlying patterns that can be
addressed systematically rather than symptomatically. Remediation efficiency: Grouping similar vulnerabilities that
can be fixed through common solutions. Development synchronization: Aligning fixes with planned
development activities to reduce context switching. Perhaps the most important realization when implementing
AppSec-as-a-Service is understanding that application security maturity
is an ongoing journey. The most successful organizations don't attempt
to leap to perfect security overnight – they build capabilities
progressively. A maturity-focused managed security approach typically follows this
progression: Assessment and visibility: Establishing a baseline understanding
of the current application security posture. Critical vulnerability remediation: Addressing the most serious
and exploitable issues. Process integration: Embedding security checkpoints into
existing development workflows. Developer enablement: Providing training and tools to help
developers write secure code from the start. Continuous improvement: Implementing metrics and feedback loops
to drive ongoing security enhancements. Not all application security service providers are created equal. When
evaluating potential partners, consider these critical factors: Technical depth: Look for deep expertise in both security and
modern development methodologies. Communication style: Prioritize partners who communicate in
developer-friendly language rather than security jargon. Business understanding: The best partners recognize security
must align with business objectives. Unparalleled Support: Your needs will evolve; ensure your partner
can adapt their services accordingly. Culture alignment: Security partners should enhance your
development culture, not conflict with it. When implemented effectively, application security as a managed service
doesn't just protect your organization – it becomes a competitive
advantage. In an era where security breaches make headlines weekly, the
ability to develop and deploy secure applications quickly creates
business differentiation. Organizations with mature application security practices: Release faster: With security integrated throughout the SDLC,
there are fewer last-minute surprises. Innovate more confidently: Teams can explore new technologies
with appropriate security guardrails. Build customer trust: Security becomes a selling point rather
than a liability. Attract talent: Developers increasingly want to work where
security is valued and well-implemented. Cypress Data Defense's Enhanced Application Security (EASy) managed
service was designed specifically to address the challenges outlined in
this article. As a comprehensive AppSec-as-a-Service solution, EASy
helps resource-constrained organizations transform application security
from a bottleneck into a business enabler. Expert Vulnerability Assessment and Validation Our security professionals don't just run automated scans – they analyze
your applications in context, eliminating false positives and providing
accurate risk assessments that matter to your business. Practical, Developer-Friendly Remediation Guidance Instead of vague security reports, your team receives specific guidance
with clear examples of how to fix identified vulnerabilities, reducing
the back-and-forth that typically slows security remediation. Seamless SDLC Integration We work with your development teams to integrate security throughout
your development lifecycle, catching vulnerabilities when they're least
expensive to fix without disrupting your development velocity. Flexible Engagement Models Whether you need comprehensive application security coverage or targeted
assistance with specific high-risk applications, our service scales to
match your needs and budget constraints. Security Maturity Development Beyond immediate vulnerability remediation, we help you build lasting
security capabilities through developer training, process improvement,
and security culture development. With Cypress Data Defense's EASy service, you gain the expertise of a
dedicated application security team without the overhead and challenges
of building one from scratch in today's competitive talent market. The old view of application security as a necessary evil that slows
development is outdated and counterproductive. With the right managed
security approach, application security becomes an enabler of faster,
more reliable development. By addressing the critical challenges of resource constraints, false
positives, and late-stage vulnerability detection, AppSec-as-a-Service
transforms security from a bottleneck into a strategic advantage. In
today's threat landscape, this transformation isn't just nice to have –
it's essential for survival and success. As you evaluate your application security approach, ask yourself: Is
security your development team's biggest constraint, or is it their
secret weapon? If it's not the latter, it's time to consider Cypress
Data Defense's EASy service as your path forward. Contact us today to get a free assessment on a sample application so you can see the power of this service: https://cypressdefense.com/contact/The Hidden Cost of the Security Talent Shortage
Why Early Detection Changes Everything
The False Positive Problem No One Talks About
AppSec-as-a-Service: The Force Multiplier
The Business Case for AppSec-as-a-Service
The Strategic Remediation Approach
Application Security Maturity: A Journey, Not a Destination
Choosing the Right AppSec Partner
Beyond Security: Competitive Advantage
About Cypress Data Defense's EASy Managed Service
The EASy managed service provides:
Conclusion: Security as an Enabler